![]() This post should be set within the Tutorials category, but as “secure” is present within the title…
This post should be set within the Tutorials category, but as “secure” is present within the title… ![]()
Introduction
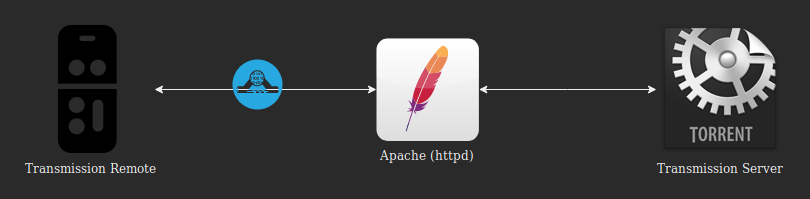
Almost three years ago, I wanted to improve a pretty basic Transmission installation made by my father, for what we call a seedbox.
Basically, the expected setup was :
-
Apache (httpd) as reverse proxy (not NGINX or anything else) ;
-
Transmission RPC service password-protected (we live in the 21st century, it’s difficult to “hide” a service…) ;
-
A connection over TLS (we are in 2018 now, communications are not really secure by design) ;
-
Transmission RPC service socket not directly listening on Internet (why the hell would you want that ?).
Back in the past, I couldn’t manage to get it working for various reasons, but anyway, now it’s done, and here is a short but complete post to guide you.
Note before going down : Apache has been chosen to handle the authentication process here (with htpasswd). This way, we don’t have to forward any HTTP header to the Transmission back-end through Apache. #keepItSimple
Transmission configuration
Let’s start with the easy part !
So the idea is about making Transmission listening on localhost only, and discharge him from handling the authentication part.
Simply edit /etc/transmission-daemon/settings.json, and modify the keys related to RPC configuration, according to :
{
"rpc-enabled": true,
"rpc-bind-address": "127.0.0.1",
"rpc-port": 9091,
"rpc-url": "/transmission/",
"rpc-whitelist": "",
"rpc-whitelist-enabled": false,
"rpc-host-whitelist": "127.0.0.1",
"rpc-host-whitelist-enabled": true,
"rpc-authentication-required": false,
"rpc-username": "NOT_RELEVANT",
"rpc-password": "NOT_RELEVANT"
}Now, you only have to take care of reloading the Transmission daemon, NOT RESTARTING IT (your changes would be overridden, as noted within the README file in the same directory) :
# systemctl reload transmission-daemon
Apache configuration
Now the tricky part !
I’ve run many many many tests to come up with a short, straightforward and comprehensive piece of configuration. You should be able to adapt it for your case pretty easily.
For a first step, we have to create credentials for the future basic authentication :
# mkdir /etc/apache2/htpasswd/ && htpasswd -c /etc/apache2/htpasswd/transmission transmission
Choose a strong password, and store it somewhere safe (as always, isn’t it ? ![]() ).
).
Now, let’s add a new VHOST (/etc/apache2/sites-available/transmission.conf) for our reverse proxy :
<VirtualHost _default_:443>
ServerName your.domain.name
<Location "/transmission/">
AuthType Basic
AuthName "Credentials for Transmission"
AuthUserFile "/etc/apache2/htpasswd/transmission"
Require valid-user
ProxyPass "http://localhost:9091/transmission/"
ProxyPassReverse "http://localhost:9091/transmission/"
# Fix for "SSL input filter read failed"
SetEnv nokeepalive
</Location>
LogLevel Warn
ErrorLog ${APACHE_LOG_DIR}/transmission_error.log
CustomLog ${APACHE_LOG_DIR}/transmission_access.log combined
SSLEngine On
SSLCertificateFile /path/to/your/fullchain.pem
SSLCertificateKeyFile /path/to/your/privkey.pem
Header always set Strict-Transport-Security: "max-age=63072000"
</VirtualHost>The “fix” you surely notice is mostly a workaround for this issue.
Don’t forget to enable the new VHOST :
# a2ensite transmission
For the given configuration above, you’ll have to enable some new Apache modules, if they are not already loaded :
# a2enmod auth_basic env headers proxy_http ssl
# systemctl restart apache2
Now reload your Apache configuration, and everything is supposed to work… From anywhere (see below) !
# systemctl reload apache2
So, now you should be able to access your Transmission WEB interface from : https://your.domain.name/transmission/web/.
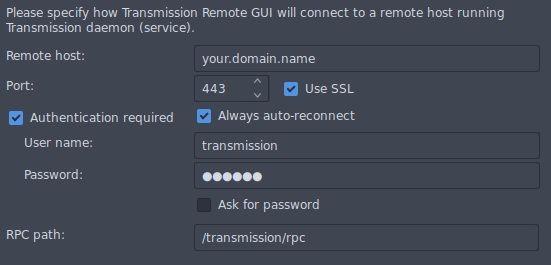
But also from a Transmission remote client that supports TLS (for instance, transgui) :
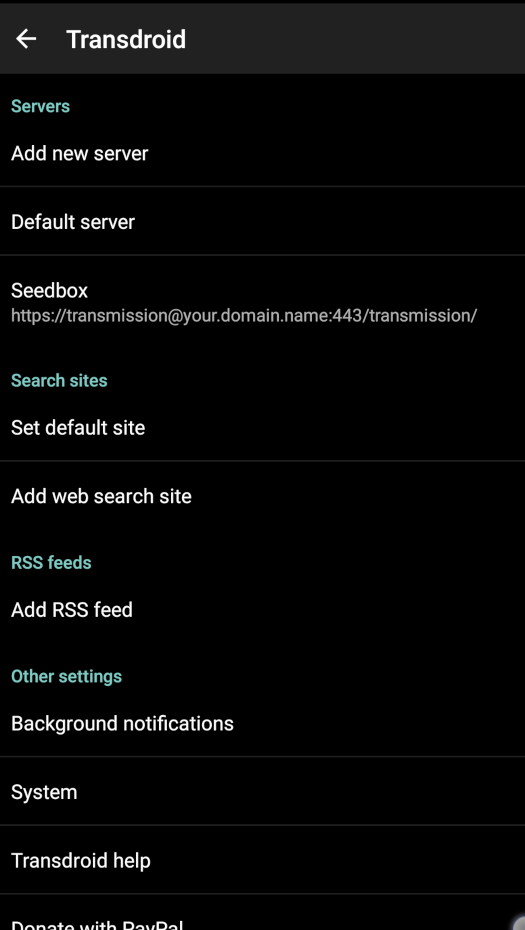
And at last (but not at least !), from an Android remote client, like Transdroid :
Pro tip 1 : You’ll have to enable the HTTPS scheme under server’s Advanced settings by checking Use SSL.
Pro tip 2 : You’ll also have to tweak the remote port value under server’s Advanced settings > Port number, by setting it to 443 to make the default 9091 disappear !
Pro tip 3 : And finally, you’ll have to tweak the remote folder path under server’s Advanced settings > Folder, by setting it to /transmission/ to match the expected VHOST location.
PS : In this guide, I have not spoken about getting a TLS certificate, nor setting up Transmission or Apache from scratch. If you need any help, or have any question, feel free to open a discussion with comments below !